Configure LDAP authentication
You can add users using LDAP authentication.
Note: users can belong both to root domain and to subdomains. If you need to add users from subdomains, use Global Catalog.
To connect to the LDAP server:
- Log in to the platform as an administrator;
In the left menu select Admin > LDAP;
Turn on LDAP connection;
Fill all the required fields:
- LDAP Protocol – connection method to the LDAP server (plain
ldapor secureldaps); - LDAP Port – port number of the LDAP server (the common value of this field is 389);
Note: when you add users from subdomains, use Global Catalog ports – 3268 or 3269.
- Host – IP address or hostname of the LDAP server;
- Base DN – catalog, in which search of users is performed. You should fill in this field with one or several attributes in LDAP syntax, f.e.
DC=host,DC=test,DC=domain; - Blocked Group DN – defines objects attribute values that will be identified as blocked user groups. Attribute values must be input according to LDAP syntax, f.e:
CN=U.ApiaryBlocked,CN=Users,DC=dc,DC=corp,DC=hexway,DC=com- Service Login – LDAP user with the right to view the content of the Base DN branch. It is recommended to use
userPrincipalNameformat (e.g.t.adm@test.domain), but you can also use distinguished name; - Service Password – LDAP user password;
- if you're using HashiCorp Vault to store the LDAP user password, follow the instruction how to integrate Vault and Apiary here
- User filter – defines objects attribute values that will be identified as users. Attribute values must be added according to the LDAP syntax, f.e.:
(objectClass=*)– the search will be done through all the available entries;(&(objectClass=user)(loginAttr=login))– the search will be done through the objects with corresponding attribute values;
Note: in most cases, the right User filter's value is
user, but if your LDAP server is not standard, try other variants.- Admin Group DN – defines objects attribute values that will be identified as user groups. Attribute values must be input according to LDAP syntax.
CN=U.ApiaryAdmins,CN=Users,DC=dc,DC=corp,DC=hexway,DC=comNote: in most cases, the right Group filter's value is
(objectClass=group), but if your LDAP server is not standard, try other variants.- Login attribute – attribute that will be used for users' authentication, f.e.
sAMAccountName– corresponds with the login format liket.adm; - E-mail attribute – attribute name that contains user e-mails, f.e.
userPrincipalName– corresponds with the login format liket.adm@test.domain;
Note: if you want to connect only to subdomain, use login in the
userPrincipalNameformat (e.g.t.adm @test.domain).- First Name attribute – attribute name that contains first username (f.e.
givenName); - Last Name attribute – attribute name that contains last usernames (f.e.
sn).
- LDAP Protocol – connection method to the LDAP server (plain
Click Test connection, to check the connection to the LDAP server. If settings are correct, you will see Connection established:
- Click
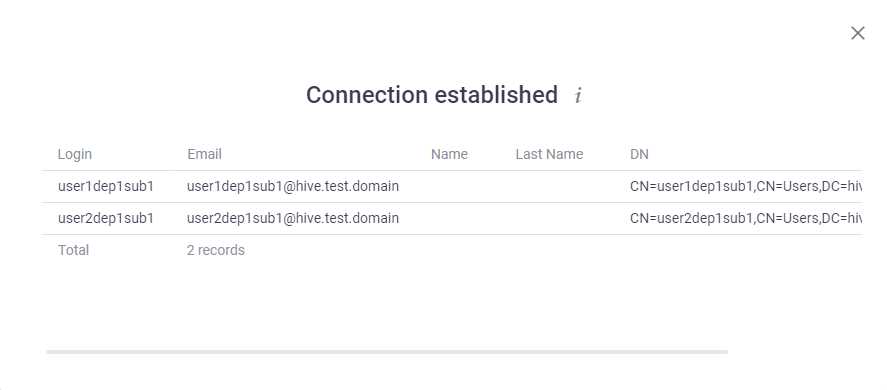
ito view all available users:
- Click
Click Save. User will appear on Users tab after the first login to the platform.
Note: after saving LDAP settings, you will not be able to add local users to the Platform.
Known LDAP Issues
- Only simple authentication is available, gss-api is not available.
Unprocessed Continuation Reference(s)error can occur when system addresses to the domain with subdomains and without Global Catalog role (e.g., to the port number 389 with valuesDC=test,DC=domainin Base DN field). To solve this error, you should indicate more specific value in the field Base DN, e.g.CN=users,DC=test,DC=domain.